Compare commits
10 Commits
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
df0a37095b | ||
|
|
e3ba27bd6c | ||
|
|
7aa7548df6 | ||
|
|
e719f111f1 | ||
|
|
ea5b7d105b | ||
|
|
8e0755466e | ||
|
|
8cee8d8672 | ||
|
|
d476766d3b | ||
|
|
04d150284f | ||
|
|
cf4738df59 |
8
Makefile
8
Makefile
@ -1,11 +1,15 @@
|
||||
.PHONY: all build
|
||||
.PHONY: all build compile quick
|
||||
|
||||
all: build
|
||||
|
||||
build:
|
||||
compile:
|
||||
CGO_ENABLED=0 GOOS=linux go build -mod=vendor -a -ldflags="-s -w" -o dist/dsnet ./cmd/dsnet.go
|
||||
|
||||
build: compile
|
||||
upx dist/dsnet
|
||||
|
||||
quick: compile
|
||||
|
||||
update_deps:
|
||||
# `go mod vendor` initialises vendoring system
|
||||
go get
|
||||
|
||||
61
README.md
61
README.md
@ -1,5 +1,6 @@
|
||||
dsnet is a simple configuration tool to manage a centralised wireguard VPN.
|
||||
Think wg-quick but quicker. From scratch:
|
||||
Think wg-quick but quicker. It can generate ready-to-go client configs for
|
||||
wg-quick, EdgeOS and NixOS. From scratch:
|
||||
|
||||
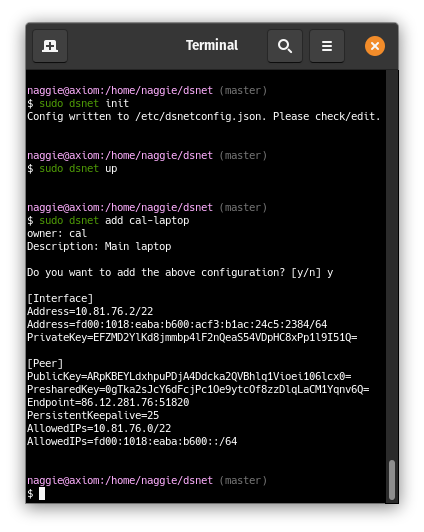
|
||||
|
||||
@ -37,8 +38,19 @@ Quick start (AMD64 linux) -- install wireguard, then, after making sure `/usr/lo
|
||||
|
||||
Copy the generated configuration file to your device and connect!
|
||||
|
||||
To send configurations, ffsend (with separately transferred password) or a
|
||||
local QR code generator may be used.
|
||||
To send configurations, here are a few suggestions.
|
||||
- [ffsend](https://github.com/timvisee/ffsend), the most straightforward option;
|
||||
- [magic wormhole](https://magic-wormhole.readthedocs.io/), a more advanced
|
||||
option, where the file never passes through another server;
|
||||
- [womroleh-william](https://github.com/psanford/wormhole-william), a Go
|
||||
implementation of the above.
|
||||
|
||||
For the above options, one should transfer the password separately.
|
||||
|
||||
A local QR code generator, such as the popular
|
||||
[qrencode](https://fukuchi.org/works/qrencode/) may also be used to generate a
|
||||
QR code of the configuration. For instance: `dsnet add | qrencode -t ansiutf8`.
|
||||
This works because the dsnet prompts are on STDERR and not passed to qrencode.
|
||||
|
||||
The peer private key is generated on the server, which is technically not as
|
||||
secure as generating it on the client peer and then providing the server the
|
||||
@ -46,8 +58,16 @@ public key; there is provision to specify a public key in the code when adding
|
||||
a peer to avoid the server generating the private key. The feature will be
|
||||
added when requested.
|
||||
|
||||
# GUI
|
||||
|
||||
Dsnet does not include or require a GUI, however there is now a separate
|
||||
official monitoring GUI: <https://github.com/botto/dsnet-gui>.
|
||||
|
||||
# Configuration overview
|
||||
|
||||
The configuration is a single JSON file. Beyond possible initial
|
||||
customisations, the file is managed entirely by dsnet.
|
||||
|
||||
dsnetconfig.json is the only file the server needs to run the VPN. It contains
|
||||
the server keys, peer public/shared keys and IP settings. **A working version is
|
||||
automatically generated by `dsnet init` which can be modified as required.**
|
||||
@ -150,10 +170,12 @@ for hugo and PHP code for rendering a similar table.
|
||||
|
||||
# Generating other config files
|
||||
|
||||
dsnet currently supports the generation of `wg-quick` configuration by default.
|
||||
It can also generate VyOS/Vyatta configuration for EdgeOS/Unifi devices such as
|
||||
the Edgerouter 4 using the
|
||||
[wireguard-vyatta](https://github.com/WireGuard/wireguard-vyatta-ubnt) package.
|
||||
dsnet currently supports the generation of a `wg-quick` configuration by
|
||||
default. It can also generate VyOS/Vyatta configuration for EdgeOS/Unifi devices
|
||||
such as the Edgerouter 4 using the
|
||||
[wireguard-vyatta](https://github.com/WireGuard/wireguard-vyatta-ubnt) package,
|
||||
as well as configuration for [NixOS](https://nixos.org), ready to be added to
|
||||
`configuration.nix` environment definition.
|
||||
|
||||
To change the config file format, set the following environment variables:
|
||||
|
||||
@ -183,6 +205,31 @@ the interface numbers will (probably) be different. The interface number is
|
||||
arbitrary, so if it is already assigned replace it with a number of your
|
||||
choice.
|
||||
|
||||
Example NixOS output:
|
||||
|
||||
networking.wireguard.interfaces = {
|
||||
dsnet = {
|
||||
ips = [
|
||||
"10.9.8.2/22"
|
||||
"fd00:80f8:af4a:4700:aaaa:bbbb:cccc:88ad/64"
|
||||
];
|
||||
privateKey = "2PvML6bsmTCK+cBxpV9SfF261fsH6gICixtppfG6KFc=";
|
||||
peers = [
|
||||
{
|
||||
publicKey = "zCDo5yn7Muy3mPBXtarwm5S7JjNKM0IdIdGqoreWmSA=";
|
||||
presharedKey = "5Fa8Zc8gIkpfBPJUJn5OEVuE00iqmXnS34v4evv1MUM=";
|
||||
allowedIPs = [
|
||||
"10.56.72.0/22"
|
||||
"fd00:80f8:af4a:4700::/64"
|
||||
];
|
||||
endpoint = "123.123.123.123:51820";
|
||||
persistentKeepalive = 25;
|
||||
}
|
||||
];
|
||||
};
|
||||
};
|
||||
|
||||
|
||||
# FAQ
|
||||
|
||||
> Does dsnet support IPv6?
|
||||
|
||||
44
up.go
44
up.go
@ -17,6 +17,8 @@ func RunPostUp(conf *DsnetConfig) {
|
||||
ShellOut(conf.PostUp, "PostUp")
|
||||
}
|
||||
|
||||
// CreateLink sets up the WG interface and link with the correct
|
||||
// address
|
||||
func CreateLink(conf *DsnetConfig) {
|
||||
linkAttrs := netlink.NewLinkAttrs()
|
||||
linkAttrs.Name = conf.InterfaceName
|
||||
@ -31,28 +33,32 @@ func CreateLink(conf *DsnetConfig) {
|
||||
ExitFail("Could not add interface '%s' (%v)", conf.InterfaceName, err)
|
||||
}
|
||||
|
||||
addr := &netlink.Addr{
|
||||
IPNet: &net.IPNet{
|
||||
IP: conf.IP,
|
||||
Mask: conf.Network.IPNet.Mask,
|
||||
},
|
||||
if conf.IP != nil {
|
||||
addr := &netlink.Addr{
|
||||
IPNet: &net.IPNet{
|
||||
IP: conf.IP,
|
||||
Mask: conf.Network.IPNet.Mask,
|
||||
},
|
||||
}
|
||||
|
||||
err = netlink.AddrAdd(link, addr)
|
||||
if err != nil {
|
||||
ExitFail("Could not add ipv4 addr %s to interface %s", addr.IP, err)
|
||||
}
|
||||
}
|
||||
|
||||
err = netlink.AddrAdd(link, addr)
|
||||
if err != nil {
|
||||
ExitFail("Could not add addr %s to interface %s", addr.IP, err)
|
||||
}
|
||||
if conf.IP6 != nil {
|
||||
addr6 := &netlink.Addr{
|
||||
IPNet: &net.IPNet{
|
||||
IP: conf.IP6,
|
||||
Mask: conf.Network6.IPNet.Mask,
|
||||
},
|
||||
}
|
||||
|
||||
addr6 := &netlink.Addr{
|
||||
IPNet: &net.IPNet{
|
||||
IP: conf.IP6,
|
||||
Mask: conf.Network6.IPNet.Mask,
|
||||
},
|
||||
}
|
||||
|
||||
err = netlink.AddrAdd(link, addr6)
|
||||
if err != nil {
|
||||
ExitFail("Could not add addr %s to interface %s", addr.IP, err)
|
||||
err = netlink.AddrAdd(link, addr6)
|
||||
if err != nil {
|
||||
ExitFail("Could not add ipv6 addr %s to interface %s", addr6.IP, err)
|
||||
}
|
||||
}
|
||||
|
||||
// bring up interface (UNKNOWN state instead of UP, a wireguard quirk)
|
||||
|
||||
Loading…
Reference in New Issue
Block a user